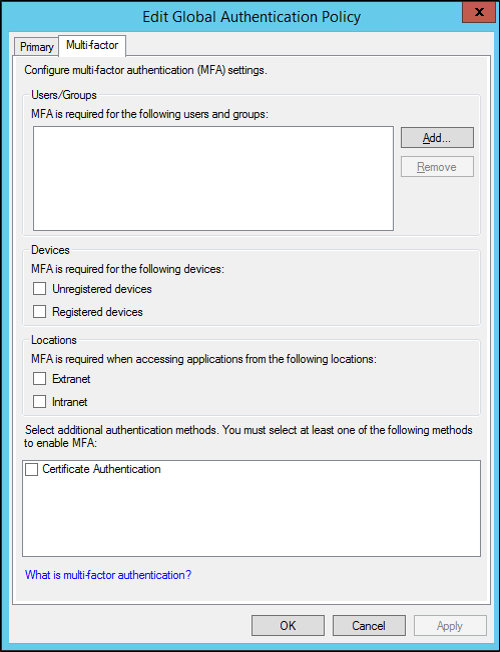
We can Configure multi-factor authentication policies on AD FS (Active Directory Federation Services) by editing each relying party trust which only affects the particular application or globally by editing Global Multi-factor Authentication ADFS server level which affects all the application on ADFS, relying party trust does not override the global authentication policy, so you have to select which one is best for your requirement, I recommended to go with global authentication policy as this covers all the relying party trusts and application on your ADFS
Also Read: ADFS 2016 failing to add secondary members to the farm with missing SPN error
MFA is based on user or group membership, registered device or Unregistered device, network location external or internal, you can select above options based on your requirement
Also Read: Windows Server 2019 Features
Enable Multi Factor Authentication Globally
- Open ADFS Management
- Select Authentication Policies
- Edit Global Multi-factor Authentication under Actions
- Select Multi-factor
- Select the conditions
- user or group membership
- device or Unregistered device
- external or internal
- Select the additional authentication method
- The default method is Certificate Authentication
- You can also configure other methods like Windows Azure Multi-Factor Authentication or RSA Authentication
Also Read: Can we Replace on-premise Domain Controller with Cloud-based Active Directory
Also Read: Compare primary and staging Azure AD connect (AADC) sync servers
Enable Multi Factor Authentication on relying party trust
- Open ADFS Management
- Select Authentication Policies
- Select Relying Party Trust
- Select the relying party trust from the list
- Edit Custom Multi-factor Authentication under Actions
- Select Multi-factor
- Select the conditions
Also Read: Active Directory 2016 New Features